Table of Contents
What is a blockchain?
Blockchain allows the instant and seamless transfer of token ownership between participants in the network. Tokens on Blockchain or Distributed Ledger Technology (DLT) consist of encrypted digital representations of information/assets.
Tokenization is the process of replacing a sensitive data element with a non-sensitive equivalent, referred to as a token. This was enabled by the digital revolution, which began in the second half of the 20th century (aka: Third Industrial Revolution).
The world shifted from mechanical and analog electronic technology to more sophisticated digital electronics through the adoption of digital computers and digital record-keeping systems. This marked the beginning of the Information Age, where the economy became primarily based on information technology.
This technological advancement contributed to establishing a new era where global exchanges between parties scaled up significantly. Consequently, processes became much more complex at a much faster pace. Tokenization and tokens by core are nothing new to our world, data has been tokenized since the creation of computers.
In a globalized, highly connected world, tokens are the foundation of digital processes, we are not aware of them as they operate in the background. As users, we do not necessarily understand the complex technology operating behind digital communication systems used to transfer value or information.
To ensure safety and security in a digitized world, intermediaries such as financial institutions, developed and maintained their own legacy systems to create databases designated to record all necessary information relating to an exchange of information or ownership between parties. We simply trusted intermediaries to carry out these transactions while maintaining its record in a safe & secure manner.
In order to guarantee high degrees of database immutability, entities must take information security into account when creating and maintaining such databases. A term that frequently shows up about IT security is the CIA Triad, which stands for Confidentiality, Integrity, and Availability.
What makes a blockchain different from a traditional database? What are blockchain consensus mechanisms? This article will attempt to answer these questions while providing a basic understanding of blockchain, database security, and the differences between blockchain consensus mechanisms.
1. Blockchain is a Highly Secure Database
A database is defined as a collection of information stored and accessed electronically from a computer system.
It is important to note that while a blockchain is a database, a database is not a blockchain. This is purely due to the fact that blockchain or DLT possesses additional features that a traditional database does not intrinsically provide.
To understand how a blockchain is much more different and resilient than a traditional database, one should first understand what measures are undertaken to secure information on a database. A set of security measures must be applied to guarantee the immutability of a database, which mainly consists of the CIA Triad mentioned above.
This article will concentrate on two components of the CIA Triad: Availability and Integrity. This will help in differentiating blockchains from other mainstream databases at a later stage.

Database Integrity
Integrity allows the protection of the database from unauthorized access, therefore preventing it from being trashed with random orders. It also consists of preventing any kind of modification or deletion of information from unauthorized parties. Additionally, it allows for any change effectuated from an authorized participant to be reversed in case it was not supposed to occur.
A simple example representing integrity for a database can be such as not having the token registry trashed with random orders related to ownership of tokens.
Database Availability
In simple terms, availability in the context of a database is the process of ensuring that data is available and not lost. Therefore, it is necessary to establish a backup/recovery mechanism storing copies of the data in question. This helps protect information from being deleted or modified by any unauthorized party. As a result, any damage that occurred to the database through unauthorized access can be corrected thanks to the other copies available.
To make this recovery process more instantaneous, multiple copies of databases are needed so they can kick in when the database is attacked or goes down. The mechanism to switch to a reliable backup system automatically is also known as failover.
2. Blockchain & DLT: A Cheaper and More Efficient Database
In general, database breaches are one of the biggest issues concerning database security. One should keep in mind that as a rule of thumb, each operator of a database is responsible for the operations occurring within their systems. Hence, it is within their duties to ensure information security.
Consequently, intermediaries were established to cater specifically to that need in regards to safely & securely exchanging information or value between multiple parties. This led to the general economy relying on third parties such as banks to monitor, safeguard and transact assets between participants while simultaneously maintaining and securing their database using traditional technological systems.
Operating such systems while maintaining the highest security standards is a complex manual process that proved costly. Naturally, these third parties would then charge their users for the costs related to providing such services.
In the context of financial services and more specifically capital markets, institutions such as the Central Securities Depository (CSD) are in charge of maintaining track of the assets ownership registry.
Hence, requiring all kinds of securities related transactions to go through CSDs, making the exchange between parties more secure but at the expense of more costly and lengthy processes.
This can present financial institutions such as banks with drastic risks as they deal with high volumes.
3. Blockchain Intrinsically Guarantees Information Security
In its most basic form, blockchain technology is a data storage system that allows the development of applications. In other words, it’s a database with additional features. The code is built in a way where instructions such as “Jack sent 1 BTC to John” are collected and recorded by a block.
Once the block is formed, it gets a signature, and the whole network verifies its authenticity where it is irreversibly recorded after validation. The database is shared with all participants in the network and is updated automatically once a block is added. All transactions collected inside that block comply with the design of the protocol of the blockchain.
Using the same set up, Ethereum blockchain runs the same instruction-making process by using smart contracts to execute other sophisticated operations. For example: Swap 1 ETH for 1 BTC.
Participants take part in the network through “nodes” that require running a program on their computer in a decentralized peer-to-peer network. Recording information on the blockchain is achieved by operating these so-called nodes, these operators are rewarded for each new information successfully recorded. Nodes automatically connect to the network to find other participants with whom the newly added information is shared.
The more the blockchain network is used, the more it grows in nodes in charge of reviewing, validating, and recording transactions. This then guarantees the availability and integrity of the database in a decentralized manner, reinforcing the ledger’s immutability.
Additionally, the network is fully decentralized and permissionless, which means that anyone can become part of the blockchain network as long as they meet specific criterias. A trustless ecosystem is created, where parties can easily and instantly exchange value or information while maintaining the highest degree of security.
Approving and recording transactions on blockchain is achieved based on a consensus algorithm that is built in the code of the blockchain protocol itself. A mainstream example would be the Proof-of-Work mechanism (POW), which is the consensus used for validating and recording transactions on the Bitcoin blockchain.
Blockchain consensus mechanisms concentrate on how the right to add data is distributed among participants of the network. It also centers around how the network validates this data as an accurate log of transactions.
All this is achieved through solving algorithms by nodes that are responsible for the process of recording and validating transactions. The latter requires computational power that is utilized to solve these set of puzzles.
If blockchain is just a database then what’s the big deal about it? Why is attention so concentrated on this ecosystem?
We strongly rely on intermediaries for maintaining immutable records of databases as they provide the necessary trust to safely & securely exchange value in a highly digitized world.
Blockchain & DLT provide trust through the code and not the entity; while simultaneously maintaining top security. A breach is made almost impossible through the underlying structure of the protocol itself and the consensus mechanisms present.
Blockchain can be considered as an evolution on top of a database, making availability and integrity intrinsically obtainable.
Understanding Different Blockchain Consensus Mechanisms
Byzantine Fault Tolerance (BFT)
To understand the Byzantine Fault Tolerance system, one must first understand the Byzantine Generals’ Problem, which is a problem that all blockchain & DLT systems must solve.
The Byzantine General Problem is a game theory dilemma that illustrates how a group of Byzantine generals may have communication problems when trying to agree on a strategy. It consists of:
- The army of Byzantium is vast and led by a few generals leading huge legions (users of the blockchain and the nodes)
- All the generals have to agree on a strategy for the army to be effective (the validators must validate a block before it gets added to the ledger)
- Generals communicate using messengers (messages can get lost, tampered with, and/or delayed)
- Some generals are bad actors and send malicious messages to the network (possible 51% attack)
- How do all generals guarantee a general’s trustworthiness? (a consensus mechanism is therefore indispensable)
- The tactic that most generals agree with is the one that will prevail (the network democratically decides the movement of the blockchain)
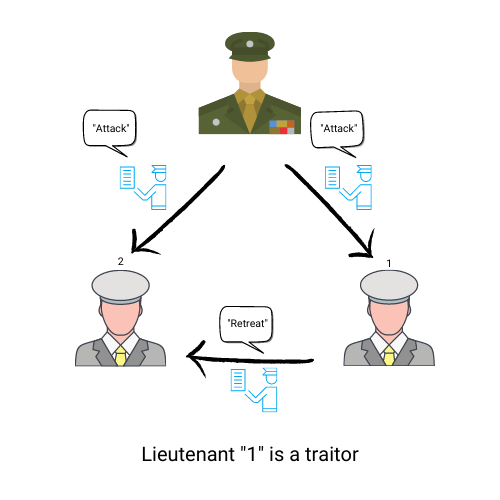
How do you ensure that at least ⅔ of generals agree on the same tactic? In the context of blockchain, how do you guarantee that the majority of nodes reach consensus by agreeing and executing the same action to avoid complete failure of the distributed network? That’s when a Byzantine Fault Tolerance (BFT) system comes into play.
BFT is the property of a system that can resist failures deriving from the Byzantine Generals’ Problem. In other words, a BFT system can continue operating regardless of the fact that some of the nodes could fail or act maliciously.
Several solutions are possible to achieve a BFT. In blockchain & DLT, it is achievable by the so-called consensus algorithms. Different blockchain protocols are composed of different consensus algorithms, a brief description of mainstream consensus mechanisms are presented below:
Proof-of-Work (PoW)
Proof-of-Work is the most popular consensus mechanism for blockchain. As mentioned earlier, it is the algorithm applied in the Bitcoin blockchain, which uses mining for recording and validating transactions. It consists of allowing secure consensus in a decentralized manner by requiring a certain amount of effort to deter malicious activities.
Nodes in the network, more specifically “miners”, have the responsibility to validate and record transactions on the ledger by solving mathematical problems in exchange for a reward generated per successful execution.
Hence the term “mining”, which consists of approving and registering transactions on the network for a cost incurred by the party issuing the transaction. Followingly, new coins are generated by the network and distributed as a form of reward among miners.
Bitcoin’s revolutionary consensus protocol, Proof of Work or Nakamoto Consensus, objectively secures the blockchain through hard mathematics applied to deterministic physics. People compete to do math in a way that can’t be shortcut until they get the chance to validate the new block.
In other words, the PoW mechanism is the process of proving that a miner has done the work needed to create a valid block (group of transactions). It is indeed hard for nodes to generate a valid block as it requires significant computational power to achieve that task.
On the other hand, it is easy for the network to verify the validity of a block thanks to the “hash function” which basically creates a unique digital signature for each block created. For a block to be accepted as valid, miners must create 2 hashes:
- A hash that represents all the transactions of a given block
- A hash proving they spent the energy needed to generate that block by solving a special cryptographic puzzle.
A hash cannot be reversed, and it confirms that each block has required work to be generated. Each block also contains the previous block’s hash, making it virtually impossible to modify a block once they are all combined in the blockchain. Modifying them would require redoing all the work done to generate every single block in the blockchain which is simply not viable.
Attacking a blockchain that runs under the PoW mechanism will require huge computational power as the attacker would require to obtain control over 51% of the nodes in charge of validating transactions to tamper with the data registered on the ledger and successfully record false transactions.
Proof-of-Stake (PoS)
The Proof-of-Stake consensus algorithm shares the same goal as PoW of reaching consensus on the blockchain. The process of reaching that goal is, however, different. PoS was introduced in 2011 to solve problems present in the PoW setup (e.g. energy consumption).
The PoS algorithm uses a pseudo-random election process to select a node to be a validator of the next block based on factors that include:
- Staking age
- Randomization
- The node’s wealth
Blocks are “forged” rather than mined. It basically requires a “forger” to be a stakeholder in the network, meaning that they own the cryptocurrency of that given blockchain. These funds are locked up into special accounts, aka staking accounts.
Nodes that have these “staked” funds can then be selected to verify blocks based on the criterias mentioned above. It is achieved similarly to the PoW systems but at a much more reduced computational power.
When a node gets chosen to forge the next block, it will check if the transactions in the current block are valid, sign the block and add it to the blockchain. Under the PoS mechanism, nodes that validate transactions are rewarded with transaction fees.
Being a stakeholder incentivizes miners to remain honest and harmless when operating network nodes. If the network detects fraudulent activity, the forger node will lose a part of its take and its right to participate as a forger in the future. As long as the stake is higher than the rewards, the validator would lose more funds than they would gain.
A 51% attack is also possible just like in PoW mechanisms, however due to the PoS nature, controlling 51% of the network is highly impractical. To gain control over the network, they would need to acquire 51% of the circulating supply.
Also, it is very likely that as soon as they gain control, the value of that cryptocurrency will plummet, and the attacker would have worthless funds. Consequently, there is no incentive behind performing such an act.
Key takeaways
Blockchain technology is a database that intrinsically enables information security through its consensus algorithm. It is by nature immutable and requires less manual intervention for maintaining it. This allows the execution of tasks automatically, instantly at a much lower cost. Learn the difference between a public blockchain vs private blockchain.
Intermediaries maintain their own databases and record-keeping systems to enable end-users with the ease of securely and safely transferring information or value between one another. Immutability of these databases is achieved through a set of information security practices put in place by these organizations.
This has however proven to be time-consuming and expensive for both users and providers.
Especially in the context of capital markets, financial institutions deal with high volumes and high security standards. This increases risk and restricts them from providing access to financial products to a diverse set of investors. Therefore being limited to only large corporate investors.
At Bitbond, we gathered the necessary expertise to develop compliant blockchain applications designated to drastically improve processes related to the issuance, custody, and settlement of financial instruments carried out by financial institutions. As we strive for improved financial inclusion, our goal is to make blockchain technology more accessible to institutions that deal with high compliance & security standards.
Get in touch with us to get a free consultation on how blockchain-based financial products and asset tokenization can improve processes within your organization. Our team of experts will advise you on the right approach to seamlessly implement such products within your existing infrastructure.




